Hello everyone! I recently passed the CPENT Exam from EC-Council and noticed a lack of comprehensive resources for exam preparation. To bridge this gap, I’ve written a detailed blog post packed with crucial information and tips to help you ace your CPENT Exam. Dive in and get the insights you need for success!


Exam Overview
- Name: Certified Penetration Testing Professional (CPENT)
- Format: Performance-based assessment
- Language: English
Flexible Duration Options
- Choose between:
- Single 24-hour intensive session
- Two 12-hour sessions for better work-life balance
Scoring and Certification Levels
- CPENT Certification: Achieve a score of 70%-90%
- Licensed Penetration Tester (LPT) Master: Excel with a score above 90%
During Exam
The total marks for the exam will be 2500, and covers following scope
- AD (500)
- Binary exploitation + IOT (500)
- CTF (500)
- OT (500)
- Pivot & Double Pivot (500)
Active Directory Range
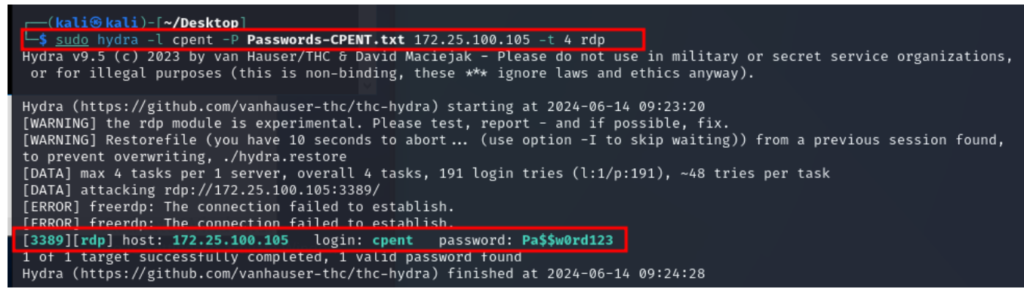
You’ll encounter practical challenges that test your ability to identify running services and exploit vulnerabilities. For instance, you might be tasked with determining the domain name of a machine at IP 172.125.10.160. This requires strategic thinking and tool utilization. You could start by using NMAP to scan for open ports and services, then employ Hydra to attempt a brute-force attack on the discovered services. Also be prepared to encounter a situation where you need to use portforwarding techniques to access the target. Understanding these methodologies and knowing when to apply specific tools is crucial for success in the CPENT exam. Practice these techniques thoroughly to enhance your penetration testing skills and boost your exam performance.
The same method can be applied to rest of the targets in the same range. The most recommended tools are NMAP, Hydra, CrackMapExec, Plink
Binary Exploitation
In Binary Exploitation tasks, you’ll work with several files. You need to use both static and dynamic analysis to find answers. While practice range focuses on .exe files, the real exam usually deals with .bin files.You’ll also need to perform account takeover or privilege escalation. For this, you can use any exploits, CVEs, or methods you prefer.These challenges test your skills in:
- Analyzing different file types
- Using various analysis techniques
- Finding and using exploits
- Gaining higher access levels in systems
Some recommended tools BinWalk, PwnKit
CTF Range
The CTF (Capture The Flag) range is my favorite. It offers a wide variety of tasks that cover everything from web exploitation to privilege escalation. This range starts with basic challenges like web-to-remote code execution (web2rce) targets. As you progress, you’ll face more complex exploits, including famous ones like ShellShock.
You can read more about this specific range here: CTF Range
Some recommended tools and CVE : Site Editor ShellShock
OT Range
The OT Range proved to be quite challenging for me. The task involved working with the ModBus protocol, requiring the use of tcpdump. However, the target machine initially had no traffic on this protocol. I had to ask the proctor to notify the tech team. After several restarts and attempts, I was finally able to capture traffic using tcpdump. The answers to the challenge can be found by analyzing the tcpdump data with Wireshark. The questions are straightforward, such as identifying the destination MAC address of the device making the ModBus request.
Recommended tools : TcpDump WireShark
Pivoting and Double Pivoting
This range presents a significant challenge, as it requires not only system exploitation but also port forwarding to successfully compromise the targets and obtain the flag. In certain instances, the target may only be accessible through a compromised machine. Therefore, in addition to the common system exploitation methods discussed in previous sections, it is essential to be prepared for port forwarding techniques.
Recommended tools: Impacket CrackMapExec
Personal suggestions
Don’t worry about practice range : There’s no need to be concerned about the practice range. I personally struggled to complete even half of the challenges in the practice range, which heightened my anxiety. However, I remained optimistic that the actual exam would be more straightforward, and indeed it was. Therefore, if you find yourself unable to clear the practice range, it’s completely acceptable. The exam range is likely to be significantly different from the practice range, so don’t let this discourage you.
Inform the proctor and clarify any doubts: During my exam, I encountered an issue accessing the target machine, and in session 2, I received only 48 questions, whereas in session 1, I had 51. I promptly informed the proctor about this and took screenshots of our entire conversation, including their reassurances. Later, I contacted the support team and explained the situation to them.
Report preparation: Attempt to prepare your report between session 1 and session 2, as the arrangements can be time-consuming, and you might overlook important details. Capture screenshots of every answer or flag, and document the steps you followed, including commands used and bruteforce results. This documentation helps demonstrate that you actually performed these tasks. While EC-Council provides a template, feel free to choose a style that you’re comfortable with for your report.
Other helpful resources
Please consider following resources,
- Rexturnull/CPENT-CheatSheet: CPENT to LPT CheatSheet
- Penetration Testing Novice’s CPENT Certificate Study Notes:: 2023 iThome Ironman Competition
- https://hackmd.io/@alrex5401/CTF_Ranger
- techbeck – HackMD
- 0xffsec Handbook: The Pentester’s Guide | 0xffsec Handbook
- https://github.com/Aviksaikat/eJPT/blob/main/notes/Penetration-Testing-Basics.pdf

